What Does This Mean Single Signon and Try Again
How single sign on (SSO) works: Definition, examples, and solutions
Password fatigue, cloud sprawl and developer simplicity are pushing the rise of SSO.

What is SSO?
Single sign-on (SSO) is a centralized session and user hallmark service in which 1 set of login credentials can be used to access multiple applications. Its beauty is in its simplicity; the service authenticates you on i designated platform, enabling you to then use a plethora of services without having to log in and out each time.
Implemented correctly, SSO can be smashing for productivity, IT monitoring and management, and security control. With ane security token (a username and password pair), an administrator can enable and disable user admission to multiple systems, platforms, apps, and other resources. SSO too reduces the risk of lost, forgotten or weak passwords.
How does single sign-on piece of work?
There are a few different standards that can be used to implement SSO, but they all follow the same bones underlying design. The key is that they make it possible for applications to hand over responsibilities for authenticating users to another application or service.
In SSO lingo, an awarding or website that a user might want to log into—anything from an e-mail client to a bank website to a network share—is a service provider . Most platforms like these include their ain functionality for authenticating users. With SSO, though, that responsibility is fielded out to an identity provider —generally, the SSO platform itself. When the user attempts to access the service provider, the service provider volition consult with the identity provider to ensure that the user has proven that they are who they claim to be. The service provider can put parameters effectually how hallmark works: for instance, it can crave that the identity provider use two-cistron authentication (2FA) or biometrics. The identity provider will either ask the user to log in, or, if they've logged in recently, may but let the service provider know that without troubling the user further.
The service and identity providers communicate via tokens , pocket-sized collections of structured information that are digitally signed to ensure mutual trust betwixt the parties. Information technology's through these tokens that the identity provider will tell the service provider that the user has authenticated—but, crucially, the tokens don't include authentication data like the user's password or biometric data. As a result, even if the tokens are intercepted by an assailant or the service provider's systems are breached, the user's password and identity remain secure. The user can as well use the same login credentials for any service providers using that identity provider.
From the point of view of the organisation administrator, the SSO platform represents a one-stop shop where user IDs tin can be managed. When an employee leaves a visitor, for example, their ability to log in to a host of internal applications can exist revoked all at one time.
Single sign-on architecture
That clarification should mankind out a moving-picture show of a single-sign on system's architecture. In the virtually common arrangement, the identity provider and service provider establish a trust relationship by exchanging digital certificates and metadata, and communicate with one another via open standards such as Security Assertion Markup Language (SAML), OAuth, or OpenID.
Writing in the Oracle Security Newsletter, Paul Toal dives deeper into SSO architectural patterns, including the less-than-ideal architectures you might need to implement if your service providers tin can't communicate with an identity provider directly.
Y'all'll likewise desire to keep in mind that your SSO platform volition have to integrate into your larger organizational Information technology architecture, and you'll need to think carefully virtually how to do so while maintaining your overall security posture. For instance, an SSO arrangement may make information technology impossible for downstream security tools to notice the originating IP accost of the user attempting to log in to your system.
Single sign-on example
You might detect that description a chip abstract. Permit'south look at a specific implementation case to see how SSO works in practice. Imagine you're the user in an environs with unmarried sign-on and you're trying to become access to some resource on a server. The sequence of events goes like this:
- You attempt to access the service provider—once more, this generally is an application or website you want to access.
- As part of a asking to authenticate the user, the service provider sends a token that contains some information nearly you, like your email address, to the identity provider, a role played past your SSO system.
- The identity provider first checks to run into whether you've already been authenticated, in which case it volition grant you access to the service provider application and skip to pace v.
- If you haven't logged in, yous'll exist prompted to practice so past providing whatever credentials the identity provider requests.
- Once these credentials take been validated, the identity provider will send a token back to the service provider, confirming that information technology's authenticated you.
- This token is passed through your browser to the service provider.
- Once received, the token is validated according to the trust relationship that was fix between the service provider and the identity provider during the initial configuration.
- The user is granted access to the service provider.
If you want a closer look at the guts of the messages beingness passed back and forth in these sorts of transactions, bank check out the examples hither from OneLogin. These examples are based on SAML; you lot tin can dig into the full XML code for the kinds of assertions being passed from the identity provider to the service provider in the scenario outlined above.
Single sign-on security benefits
SSO'due south biggest security benefit in the enterprise is that it allows an organization to scale up the number of users—and the number of associated logins—without either sacrificing security or condign bogged downwards in endless account provisioning. Thanks to automated credentials direction, sysadmins are no longer required to manually take care of all the employees' access to the services they desire. This in turn reduces the human error factor and frees up It time to focus on more important tasks.
Other benefits include rapid provisioning for cloud-commencement applications; if your SSO implementation supports the rise of open standards like SAML ii.0, the application can exist speedily provisioned past an SSO admin and rolled out to employees. SSO can likewise be combined with 2FA for increased security, and can provide productivity gains and fewer Information technology help desk password resets.
It would be wrong to propose that SSO is a silvery bullet, however. Challenges around implementing SSO include cost, control, standardization (SAML vs OAuth), and, yes, security. Hallmark flaws, similar the Sign in with Apple tree vulnerability or the Microsoft OAuth flaw could allow an assaulter to log into a site or service as though they were the victim they were targeting.
Unmarried sign-on solutions
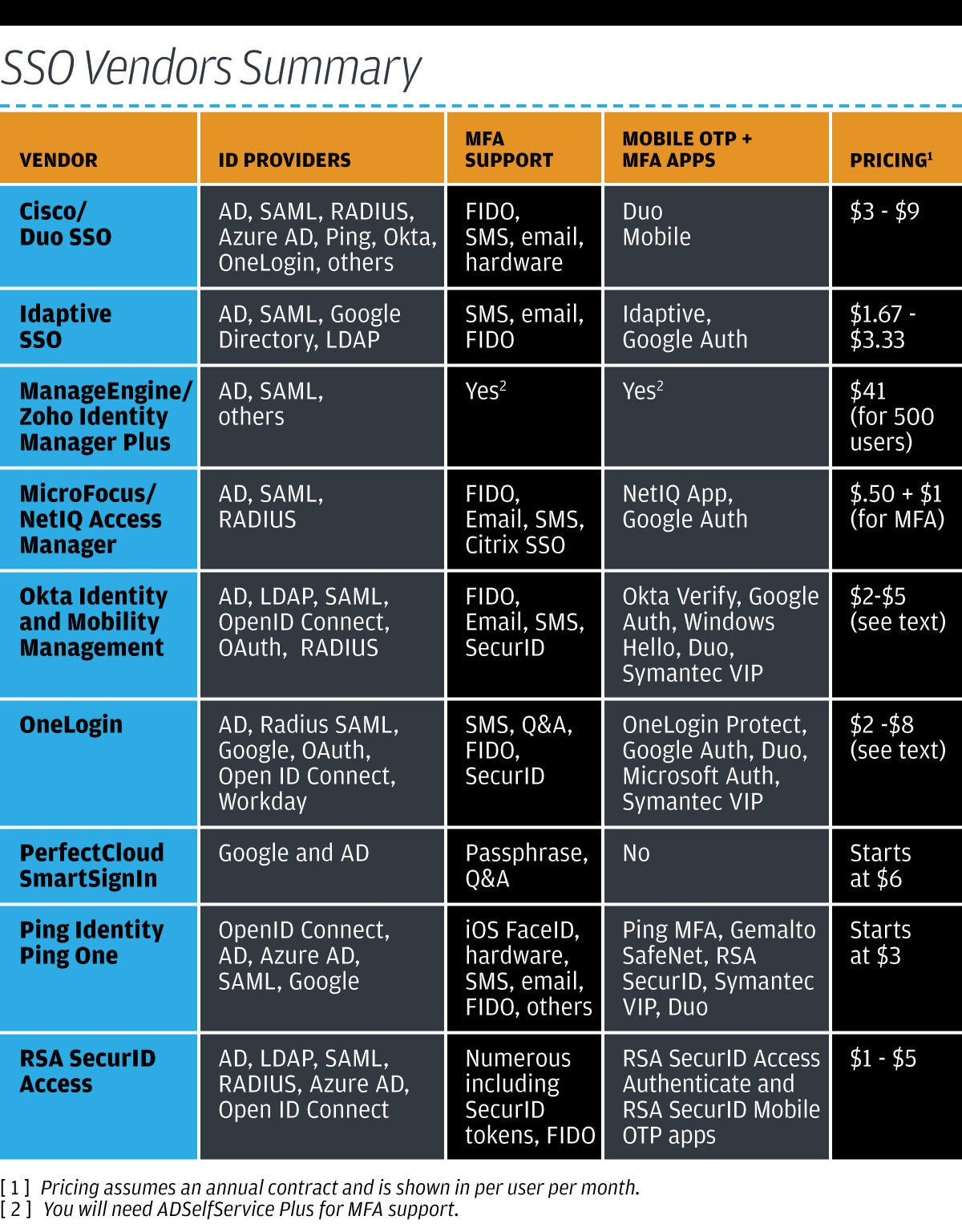
In that location are several types of SSO solutions to consider, from commercial offerings to curl-your-own open source platforms. For more on how some top SSO tools stack upwards and different approaches and considerations, run into "Single sign-on solutions: How 9 height tools compare."
SSO tools from top vendors include:
- Duo/Cisco SSO
- Idaptive Single Sign-On
- ManageEngine/Zoho Identity Manager Plus
- MicroFocus/NetIQ Admission Manager
- Okta Single Sign-On
- OneLogin Single Sign-On
- PerfectCloud SmartSignIn
- Ping Identity PingOne
- RSA SecurID Access Suite
 CSO / IDG
CSO / IDG For more on SSO, see:
- v best practices to secure unmarried sign-on systems
- Single sign-on solutions: How nine top tools compare
- iv hallmark use cases: Which protocol to use?
- What is SAML? How it works and how it enables single sign on
- What is OAuth? How the open authorization framework works
- What is IAM? Identity and admission direction explained
Copyright © 2021 IDG Communications, Inc.
Source: https://www.csoonline.com/article/2115776/how-single-sign-on-sso-works-definition-examples-and-solutions.html
0 Response to "What Does This Mean Single Signon and Try Again"
Post a Comment